IT-consulting is required by companies of various sizes, which wish to get a stable result and improve the quality of their work. Investing money in IT infrastructure does not always bring the desired result. The system as failed, and still fails, the risk of information leakage increases, the quality of work of employees decreases due to technical problems.
The way out is to engage third-party specialists who will prepare the terms of reference for IT infrastructure audit, perform physical security, server and information infrastructure checks according to the approved plan.
When IT audit is needed
- IT infrastructure costs are increasing, but performance is not increasing or is decreasing, work is unstable.
- Outdated solutions are used, there is a long-standing “mush” of codes.
- There is no clear IT architecture.
- It is difficult to build teamwork due to lack of performance.
- High developer workload, unable to solve current business tasks promptly.
- No transparency of interaction with contractors.
IT audit objectives
- Development of a strategy to improve business efficiency.
- Identification of problem areas, analyzing their criticality.
- Prevention of failures.
- Timely modernization of IT infrastructure.
- Standardization, certification.
- Improvement of information security.
- Reduction of IT implementation costs.
- Assessment of IT specialists’ competence.
Types of IT-audit
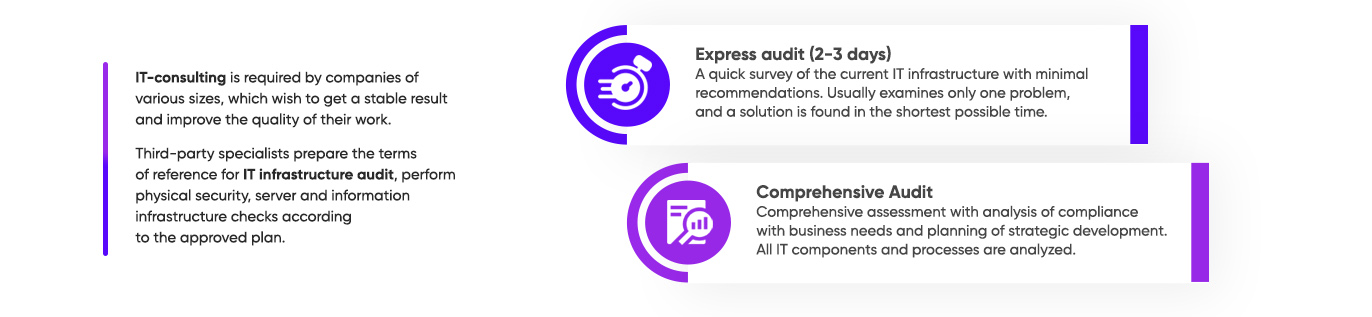
Express audit (2-3 days). A quick and superficial survey of the current IT infrastructure with minimal recommendations. Usually examines only one problem, as a result of which it is quickly localized and a solution is found in the shortest possible time. Most often used for backup, antivirus, banking, and hardware redundancy issues.
Comprehensive Audit. Comprehensive assessment of infrastructure with analysis of compliance with business needs and planning of strategic development. All IT components and processes are analyzed (correctness of IT architecture, standardization, security level, qualification of employees, causes of failures).
A special case of a comprehensive audit is a targeted audit of business processes (personnel, software, computer equipment, etc.) and selected criteria (security, performance, speed, etc.). It is conducted over a period of one to two months. It is required to find solutions to eliminate chronic problems.

The audit of the IT infrastructure of the enterprise is conducted for:
- technical systems (inventory);
- security systems (including backup, fault tolerance, data storage / delimitation, protection from external threats, etc.);
- accounting department (compliance of IT systems with the law);
- telephony and communication channels (corporate telephony and mail, messengers);
- website in terms of Internet marketing (including call center protection, building end-to-end analytics and autofunnels, checking integration schemes of web applications with company resources, DDoS attack risks, etc.).
The result of the infrastructure solutions audit analysis are recommendations on standardization of processes and ways to improve performance, achieve economic benefits, risk assessment. All consulting work is recorded in a set of technical documentation and a report on the audit of the IT infrastructure of the enterprise.
The company receives accurate information about the material base, personnel qualification, analysis of work with business data, verification of network resources and software. The obtained result is used for further modernization of the IT infrastructure.